BugKu-WEB-源代码

BugKu-WEB-源代码
题目

思路
题目提示看源代码,看源代码,发现传递方式是POST,而且有一段编码,也有一段脚本,考察代码审计
1 | <script> |
这个代码一眼过去就像html的编码,打开赛博大厨解密一下,发现几段脚本
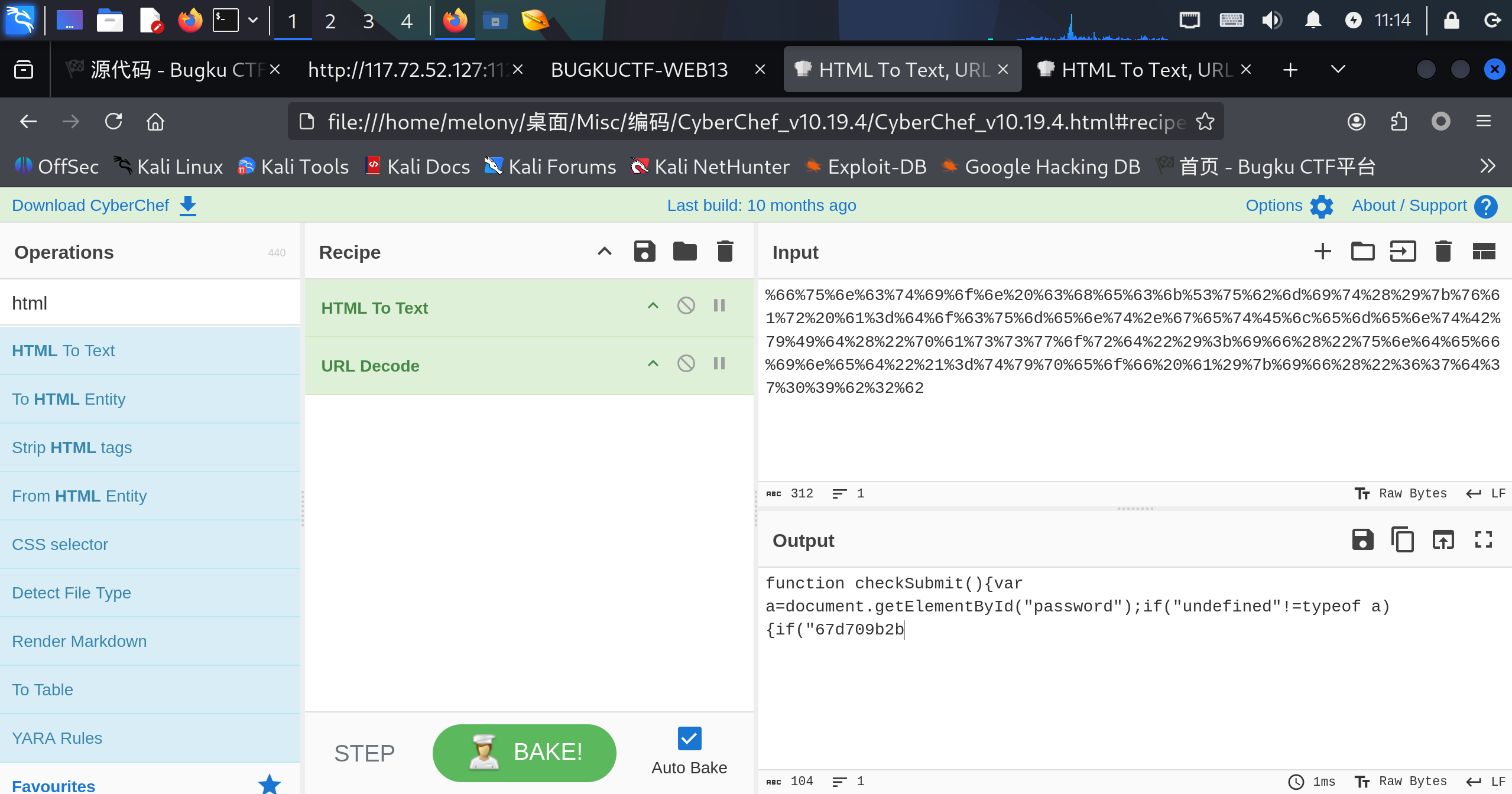
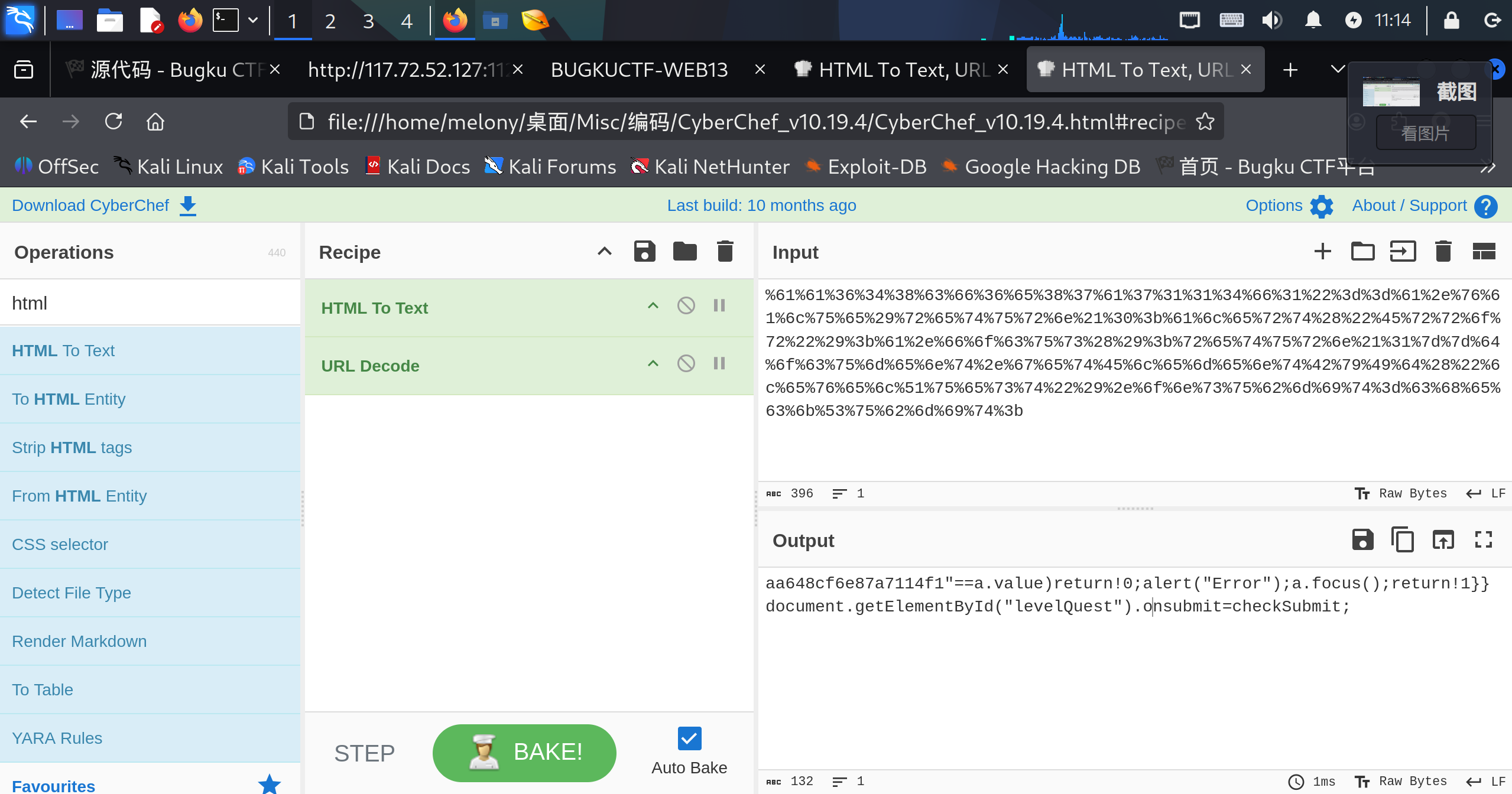
1 | function checkSubmit(){var a=document.getElementById("password");if("undefined"!=typeof a){if("67d709b2b54aa2aa648cf6e87a7114f1"==a.value)return!0;alert("Error");a.focus();return!1}}document.getElementById("levelQuest").onsubmit=checkSubmit; |
javascript中的eval()函数代表着把字符串当代码来执行,也就是上面的代码
现在来分析这个javascript
大概意思就是密码框输入的是”67d709b2b54aa2aa648cf6e87a7114f1”这个字符串,就返回true,提交表单
输入字符串,发现返回了flag
Flag
1 | flag{8aeb80c7baa47ed2e5a4e91d995b9b72} |
- 标题: BugKu-WEB-源代码
- 作者: Mel0ny
- 创建于 : 2025-09-01 11:05:26
- 更新于 : 2025-09-01 11:33:11
- 链接: https://mel0nyrame.github.io/2025/09/01/BugKu-WEB-源代码/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论